You can use the Deploy Agent Software feature to install the Agent software via the Backup Manager interface. This feature is available directly from the Protected Machines page in the Actions menu for a protected machine.
The Deploy Agent feature remotely deploys the Agent to a Linux Server and authorizes the current Backup Manager. You can select Deploy Agent Software in the Actions menu for a protected machine if at least one machine has been added and the machine does not already have the Agent installed.
| Note You can also deploy the agent software when adding a protected machine on the New Machine page by selecting the Deploy agent software now check box. Click here for more information. |
| Note Users who have Debian installations should note that a Debian-based machine that has both RPM and DEB packages installed is recognized as RPM-based only by Server Backup Manager. |
Follow the instructions below to deploy an Agent from your Backup Manager.
1. Click Protected Machines in the Main Menu to access the Protected Machines page. All existing machines will display on this page.
2. Click the Actions icon for a protected machine and select Deploy Agent Software. 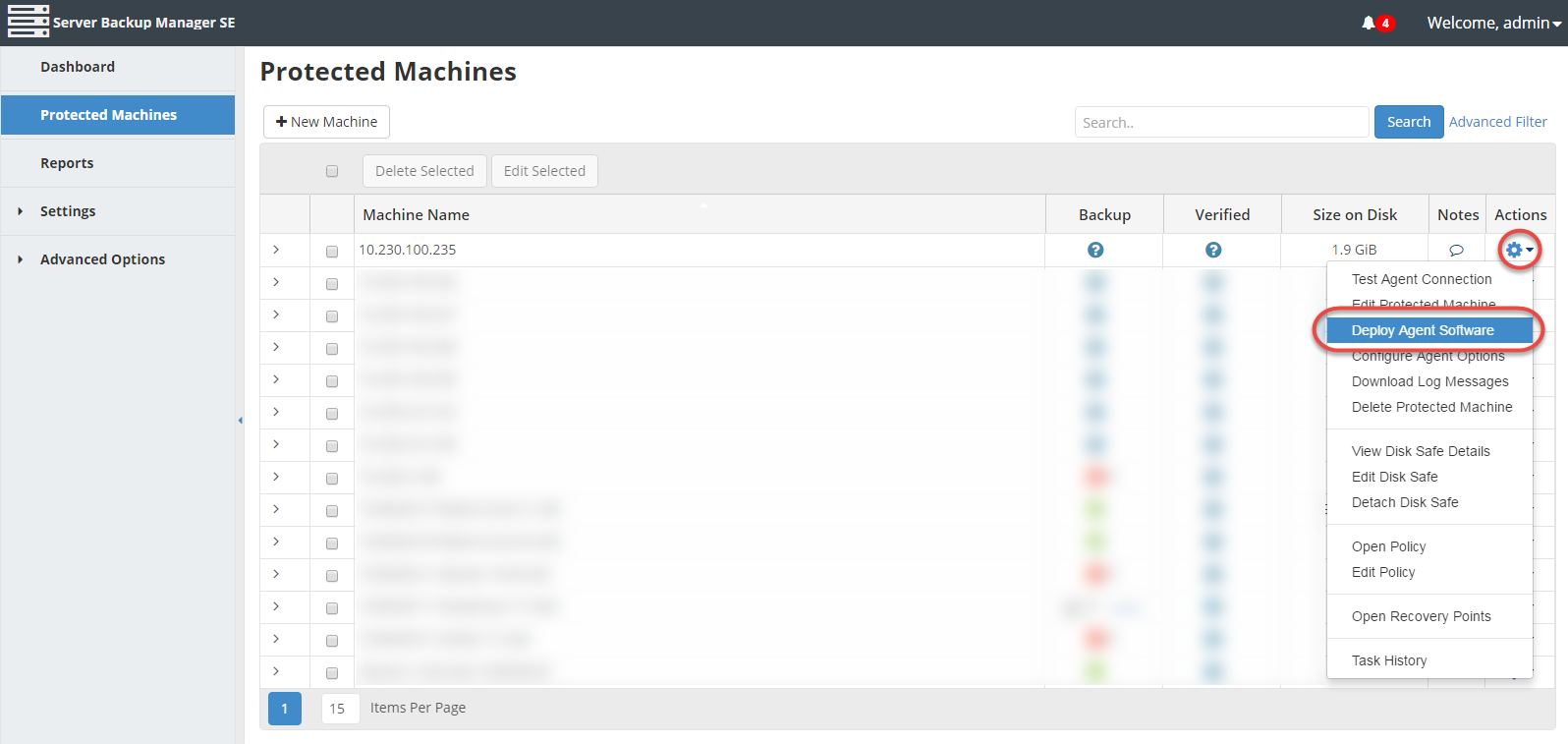
3. The Remote Agent Deployment window displays.
In the Username and Password fields, enter the username of an administrative user with access to install the Agent software on the target machine, and then enter their password. (Linux machines do not require a reboot, so you can ignore the "Reboot Windows servers after deployment" check box.)
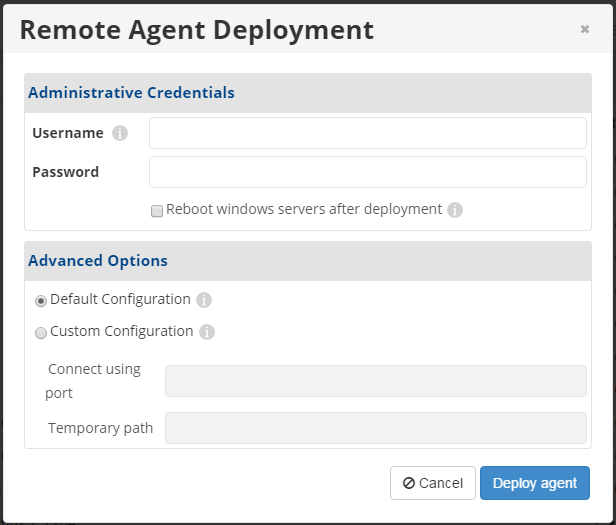
4. In the Advanced Options section, select one of the following options:
- Default Configuration. On Windows, the user's temp directory is used to store the installers by default. We use /tmp to store the installers by default. If the directory doesn't exist or doesn't have enough space, the user's home directory will be used to copy the installers. The port number is not required for Windows deployments. The default port used for connecting to a Linux machine is 22.
- Custom Configuration. Select this option to use a custom configuration for the deployment and make entries in the following fields:
- Connect Using Port. If you are connecting to a Linux machine, enter the port number that will be used to connect to the target machine. The port number is not required for Windows deployments.
- Temporary Path. The temporary path is where we store installers during deployment. The path should be absolute and already exist. If there is not enough space available to store the installers, the deployment will fail.
5. Click the Deploy Agent button to continue.
The deployment process will begin. The Details for Remote Agent Deployment window displays the report. 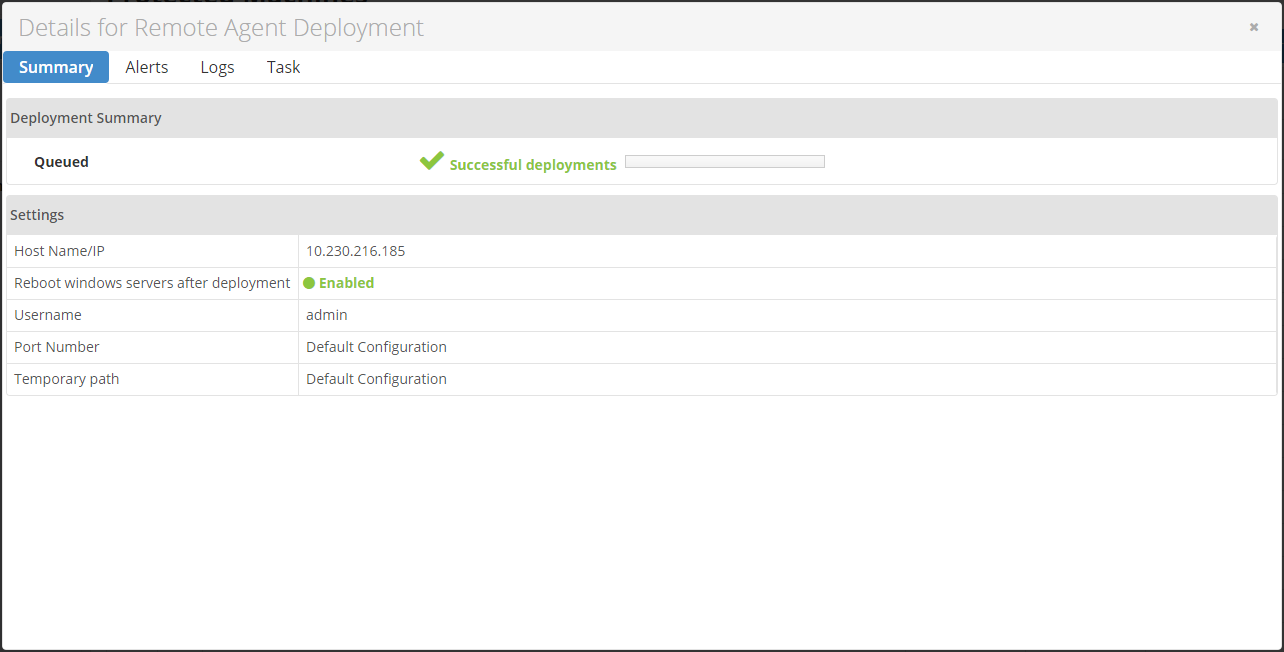
| Note You can see the result of this task in the Task History. See Access task history. |
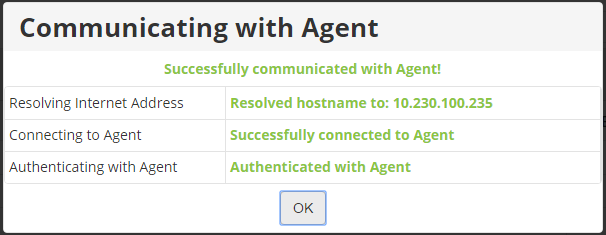
6. When the deployment process is complete, you can confirm the Agent was deployed on the Protected Machines page. Click the Actions icon for the protected machine and select Test Agent Connection.
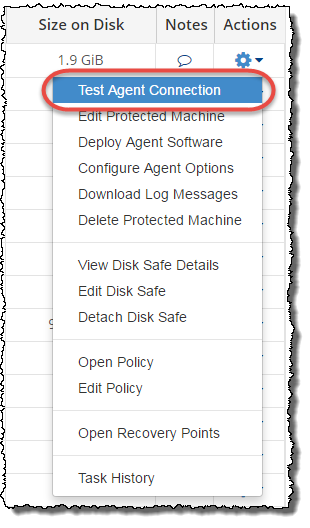
The Communicating with Agent window displays, where the status of the Agent can be reviewed.
Proceed to the next step:
