LDAP authentication can be used to verify your users against a database such as Active Directory. Once you set up your configuration on the LDAP Authentication screen, you can use LDAP authentication when adding or editing your user accounts located in a separate database. For more information about activating LDAP authentication for a user account, see Add users.
Backup Manager uses the server host name and port number to produce a URL used for authentication in the following format: ldap://<hostname>:<port number>. You can choose to use SSL/TLS to encrypt communications with the LDAP server. Backup Manager also lets you select whether you want to transmit user passwords in plain text or a hashed version of the password.
It is important that you have the base distinguished name that you want to use to authenticate LDAP users. For Active Directory servers, the base DN is typically in the format @domain.tld. For OpenLDAP servers, the base DN is typically in the format DC=domain,DC=tld. Backup Manager uses the base DN and bind attribute to determine the full distinguished name used to authenticate the user. If you specify a bind attribute, the full distinguished name is in the format <bind attribute>=<username>,<base DN>. If you do not specify a bind attribute, the full distinguished name is in the format <username><base DN>.
Configure LDAP authentication
Follow the instructions below to configure LDAP authentication for the Backup Manager.
1. In the Main menu, click Advanced Options and select LDAP Authentication. The LDAP Authentication screen displays.
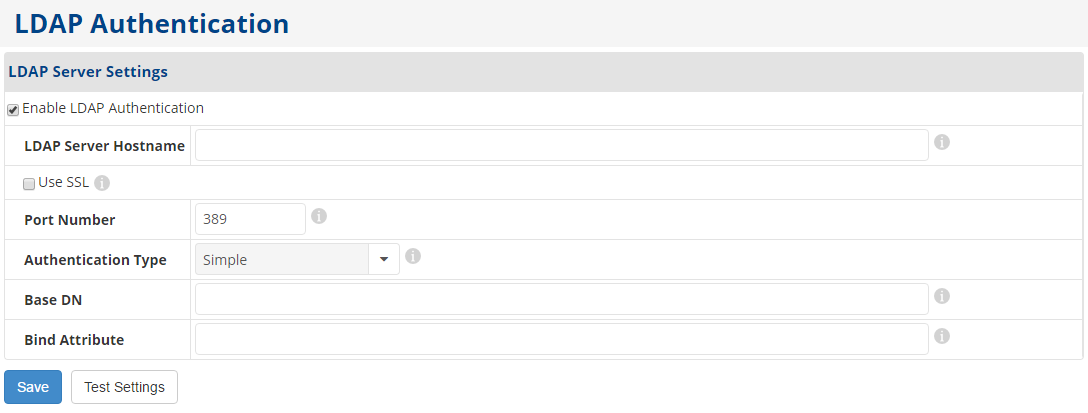
2. Select the Enable LDAP Authentication check box to use LDAP authentication.
When this check box is cleared, the other fields retain their contents but are grayed out to show that they are inactive. This feature allows you to enable LDAP authentication again without re-entering the associated data.
3. In the LDAP Server Hostname field, enter the host name of the server used to authenticate LDAP users.
The hostname will be combined with the port number to produce the URL used for authentication. The URL uses the following format: ldap://<hostname>:<port number>
4. (Optional) Select the Use SSL check box if you want to use SSL/TLS to encrypt communications with the LDAP server.
5. In the Port Number field, enter the port number used to authenticate LDAP users.
The port number entered in this field is typically 389. If the LDAP server is using SSL, the port number is typically 636.
6. In the Authentication Type field, select one of the following types of authentication used to authenticate LDAP users:
- Simple. Transmits the password in plaintext.
- Digest-MD5. Transmits a hashed version of the password.
7. In the Base DN field, enter the base distinguished name used to authenticate LDAP users.
For Active Directory servers, this is typically in the format @domain.tld. For OpenLDAP servers, this is typically in the format DC=domain,DC=tld. This is combined with the bind attribute to determine the full distinguished name used to authenticate the user. If a bind attribute is specified, the full distinguished name is in the format <bind attribute>=<username>,<base DN>. If you do not specify a bind attribute, the full distinguished name is in the format <username><base DN>.
8. In the Bind Attribute field, enter the bind attribute used to authenticate LDAP users.
This field is optional for Active Directory servers using @domain.tld for the base DN.
For OpenLDAP servers, this attribute is typically uid.
9. Click the Test Settings button to verify your server settings against an existing user account.
The Test LDAP Server Settings window displays.
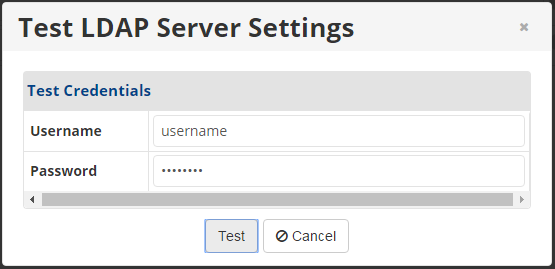
10. Enter a username and password in this window and click the Test button.
If the test is successful, the window will close.
11. After a successful test, click the Save button on the LDAP Authentication screen to save the LDAP configuration.
